Structural Digital Database Software
As per the latest SEBI PIT Compliance
1. Overview
In today’s fast-evolving capital markets, ensuring strict compliance with SEBI’s Prohibition of Insider Trading (PIT) Regulations is critical to uphold market integrity and protect stakeholders. Our Structural Digital Database Software offers a robust, secure, and scalable platform that helps organizations effectively manage insider information, monitor trading activities, and generate compliance reports — all in one unified system.
2. Key Features
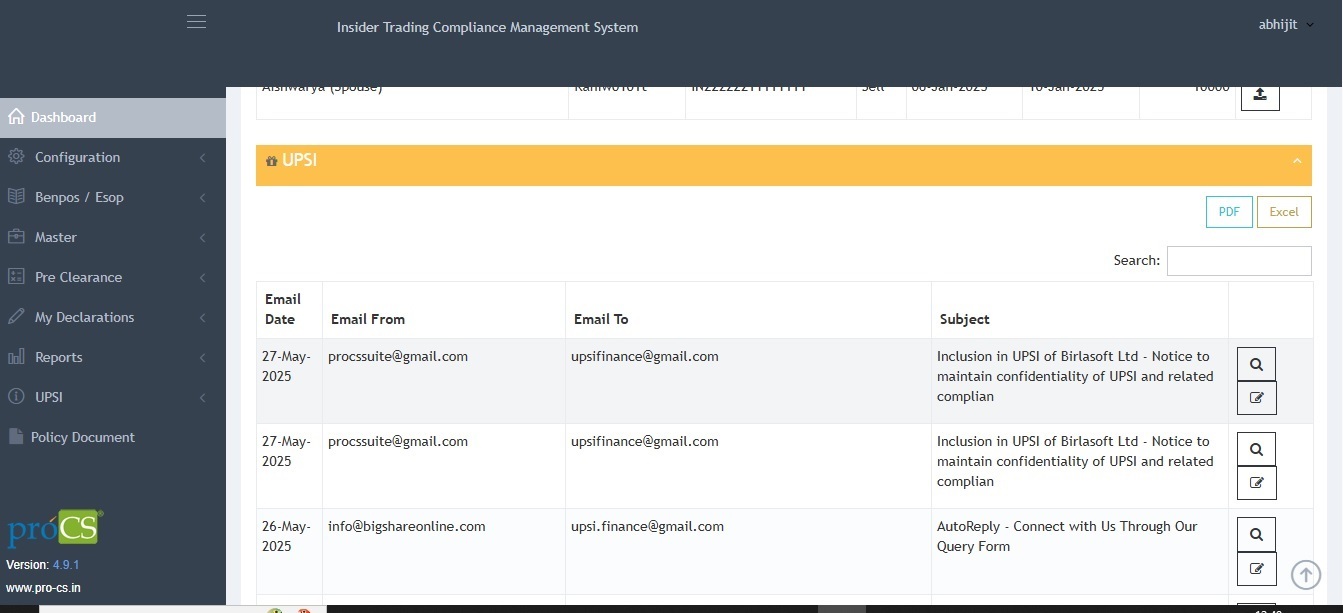
Centralized Data Repository
- Securely store all UPSI (Unpublished Price Sensitive Information) in non-temperable structured digital database.
- Maintain a historical log for audit and compliance verification.
Role-Based Access Control
- Granular access permissions to ensure that only authorized personnel can view or modify sensitive information.
- Dynamic user roles aligned with SEBI guidelines.
Automated Compliance Workflows
- Capture UPSI data via e-mails in an automated manner (No manual entry required)
- Automated alerts for blackout periods and trading restrictions.
Real-time capturing of UPSI
- Instant capturing of UPSI data via e-mails. No non-compliance due to delayed entries.
Comprehensive Audit Trail & Reporting
- Detailed logs of all the captures UPSI
- Ready-to-use compliance reports tailored to SEBI PIT requirements.
- Exportable reports for internal audits and regulatory submissions.
Integration Capabilities
- Seamless integration with existing ERP, HRMS, and trading platforms.
- API support for custom workflows and data exchange.
Data Encryption & Security
- End-to-end encryption to protect sensitive data at rest and in transit.
- Compliance with industry-standard security protocols and SEBI guidelines.
3. How It Works:
- Data Capture: Capturing of UPSI data via email automation, manual entries and through excel templates.
- Access Management: Assign user roles based on hierarchy and compliance needs.
- Monitoring & Alerts: Detect and report suspicious activities in real-time.
- Reporting: Generate detailed audit reports and submit to regulators as required.
